The Security Dashboard is the heart of the Security Audit Platform and gives you an overview of your customer's current IT security situation.
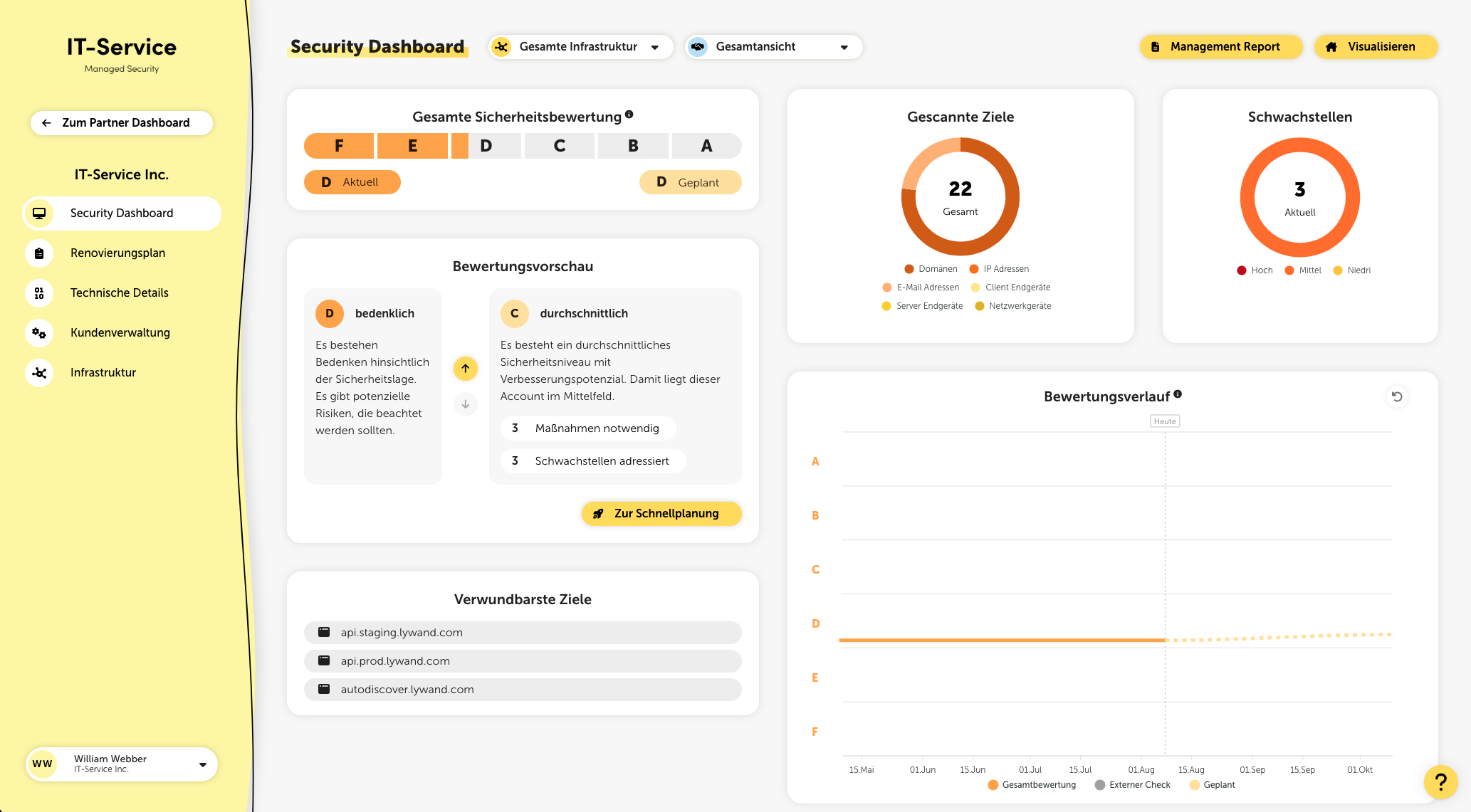
At the top of the page, you can choose between the overall view and the display of your managed services. The selected setting remains in the browser used across the entire platform and refers to relevant metrics such as the security rating or vulnerabilities found.
With the global filter up at the top next to the title, you can filter the shown data by external, internal or the whole infrastructure.
After finishing a security check, all found vulnerabilities get classified, summarized and rated according to their urgency, properties and systems affected. This way, you get an overall rating of the customer's security situation, which is shown on the Security Dashboard using a rating scale. Lywand uses a school grading system from A to F, where F is the worst rating.
To check the details of the assessment, click on the info icon in the “Overall Security Score” widget.
Score
The score is based on a scale from 0 to 10, which maps linearly to grades A through F. The higher the score, the higher the security risk and the worse the rating.
Score calculation
The score comes from the total of vulnerability risks. Higher risks are weighted exponentially higher. So, it’s not the number of vulnerabilities that matters, but the risk of each one. To significantly improve the score, you should fix the highest risk issues first.
A (outstanding)
An outstanding level of technical security was achieved and (almost) no security vulnerabilities were found.
B (good)
A good level of security was achieved and the IT infrastructure is equipped with reliable security measures.
C (acceptable)
There's an acceptable security level that’s above average. Still, there’s room for improvement.
D (concerning)
There are concerns about the security situation. There are potential risks that should be kept in mind.
E (alarming)
There are alarming security gaps that might be exploited. Immediate action is urgently needed.
F (critical)
Critical security gaps were found that could probably be exploited. Immediate action is required.
In the evaluation preview you’ll find descriptions of all rating levels plus info on how many actions you need for each level and how many vulnerabilities get covered.
This metric shows you which CIS Controls are met across all your targets. Clicking it takes you to the Best Practices page for more details.
Top right you’ll see an overview of the number of checked targets, broken down by domains, IP addresses, email addresses, and devices. There’s also an overview of open vulnerabilities with risk levels and (if enabled) the number of auto-fixed vulnerabilities via Auto Healing.
The rating history gives you info about how the security situation has developed over time. There are three areas: external, internal, and overall rating. If you hover your mouse over the gray dots, you'll find even more details about the external scan.
External: Shows all the external checks as dots (snapshots).
Internal: Shows all the internal checks as a line (daily), including company-wide vulnerabilities based on questionnaires (for example: ransomware).
Overall rating: Shows the combination of external & internal rating as a line.
Planned: Shows the possible rating after doing already planned actions as a dashed line.
This metric shows you the average time since the last check, averaged across all targets. The lower this value is, the more up to date your results are.
This metric gives you an overview of the coverage of checks performed on all your targets. The higher the percentage, the more of your targets have already been checked.
In addition to the general security rating, the security gaps found are also divided into different categories and rated.
Letters & fill levels
Capital letter & front level in orange: Category rating
Small letter and back level in salmon: Possible rating that can be reached with the planned actions
Symbols
?
Questionnaires still have to be filled out to get a rating and then actions for the category.
!
Actions should be planned ASAP in the category, 'cause right now the rating is bad.
-
No actions have been planned yet.
✓
All necessary actions have already been planned, or no actions are needed because there are no weaknesses in this category.
Here you'll find a more detailed description of each category.
This list gives you info on the five most vulnerable targets in your IT infrastructure. Click on a target to jump straight to the check insights for it.
This list gives you info on the five most vulnerable products. If you click on a product, you'll go straight to its vulnerabilities, filtered by that product.