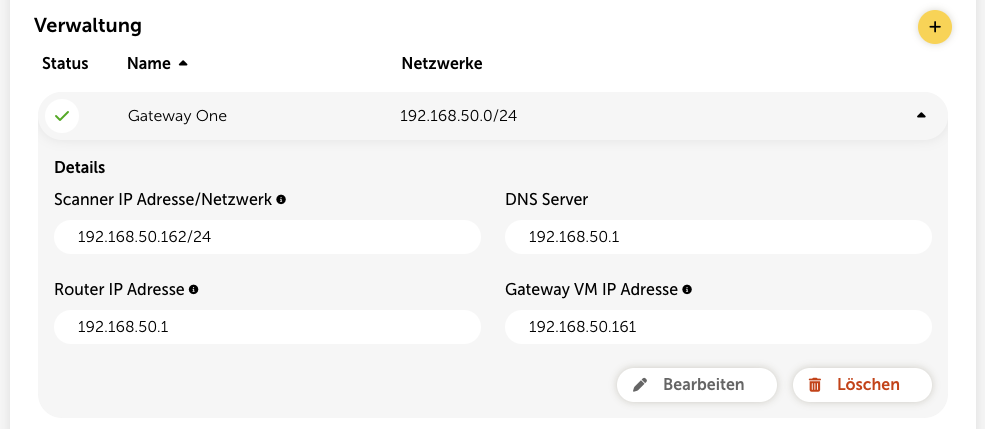
To do internal network checks, you first need to set up a special gateway VM. You can also set up several gateway VMs for different network segments. This way, you can control exactly which networks are checked by which gateway.
To set up a gateway, go to the configuration page by clicking on the “Configuration” button at the top right of the infrastructure page for internal network targets. In the “Gateways” section, you will find the necessary steps, which are described in more detail below.
Preparation
Before you set up the network check, make sure network devices are in your target overview. You can either add devices automatically using Asset Discovery or add them manually.
Then, just click the yellow plus button to create a gateway.
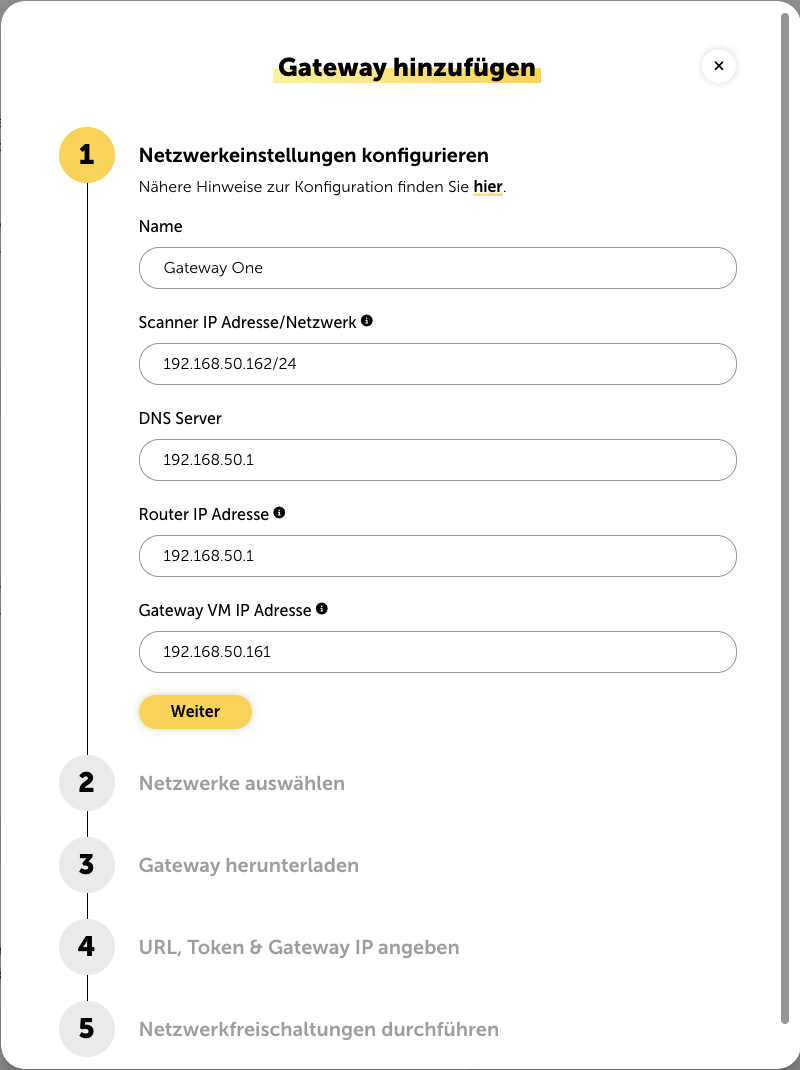
Step 1: Configure Network Settings
A setup wizard will pop up to add a gateway. In the first step, you'll set the name of the gateway and configure the necessary network settings:
The IP address of the scanner has to be a free IP in the subnet of the gateway VM. Enter the IP address with the subnet prefix. The network check will then run using this scanner IP.
This is also where the IP addresses of the DNS server and the router IP address are entered. Depending on your network setup, these IPs can be either the same or different.
Additionally, the IP address of the gateway VM needs to be entered. Make sure this is definitely different from the scanner IP! Also, the gateway VM IP address needs to be configured directly in the gateway in the next steps.
After entering the IP addresses, just click “Next” to move on to the next step.
Step 2: Select Networks
In the second step, you decide which networks should be checked by this gateway. You can either select networks from the dropdown menu that were found via Asset Discovery, or add new networks manually. Click "Next" to move on to the next step.
Step 3: Download Gateway
Once a gateway has been registered for you, just click the yellow download button to choose your preferred format and download the VM. You can pick between OVA, VHD, and ZST. You can set up the VM on any virtualization platform that's compatible with one of those file formats. We recommend using VMware (OVA), Hyper-V (VDH) or Proxmox (ZST).
You can also download the gateway images directly via the following links:
Step 4: Specify URL, Token & Gateway IP
The rest of the setup happens right in the VM. To do this, you need to set it up first and connect it to the network:
Gateway VM Installation
The VM is provided as a VMware (OVA), Hyper-V (VHD) and Proxmox (ZST) compatible image and can be imported easily. The minimum resource requirements are:
CPU: 2 cores
RAM: 2 GB
Disk: 8 GB
Gateway VM Network Configuration
Once the Gateway VM is running, you can log in with these user credentials:
Gateway login: admin
Password: admin
It's recommended to set the VM to use a static configuration. Just follow these steps:
Go to the first menu item “Network Configuration”.
Go to the second menu item “Manual Configuration”.
Configure these fields:
(Available) IP address
Subnet mask
DNS (IP address of your DNS server)
DNS name (your domain)
Gateway (IP address of your router)
Confirm the configuration with “OK”.
If you don't want to configure your VM statically, you can enable DHCP in the first menu item “Network Configuration” and then continue with the gateway configuration.
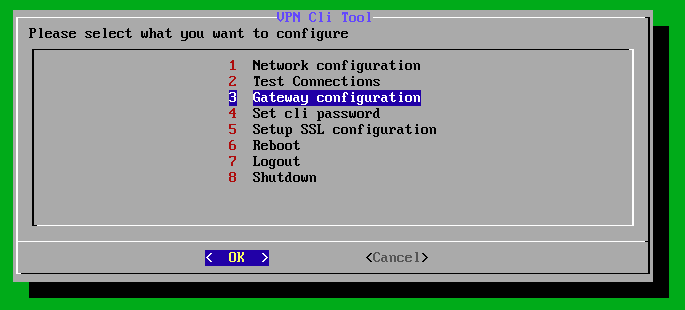
Register Gateway VM
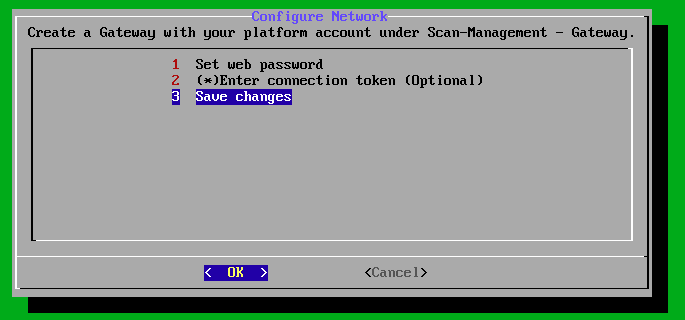
Go to the third menu item “Gateway Configuration”.
Then, switch to the second menu item “Enter connection token (Optional)”.
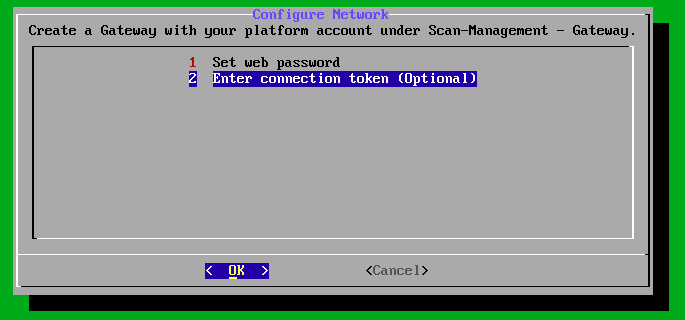
Enter the URL and token that you see in the lywand platform here and confirm by clicking “OK”.
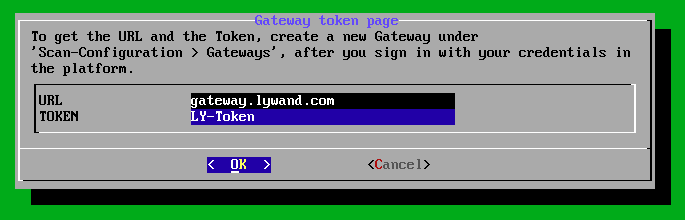

After that, switch to the third menu item “Save changes” and confirm with “OK”.
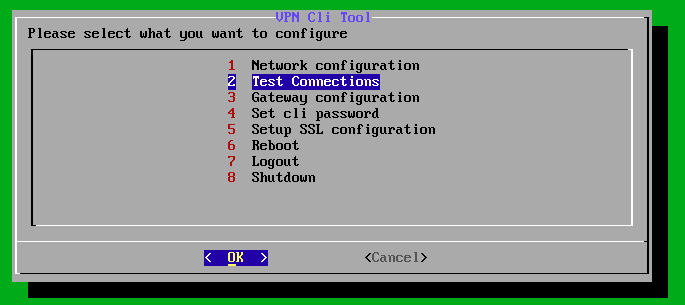
To test the general connection to the gateway, you can also use the second menu item “Test Connections” afterwards.
Step 5: Set Up Network exceptions
In the last step, you need to make sure the necessary network permissions are enabled on your firewall.
The scanner IP address and the gateway IP address must be able to reach the devices in the internal network.
The gateway IP address must be able to reach external addresses. The following firewall permissions are required for this:
443/tcp outgoing to 45.135.106.140
443/tcp outgoing to https://gateway.lywand.com (217.72.202.36)
443/tcp outgoing to https://gpublic.azurecr.io (Update Service)
With a single click on “Done”, the setup is finished. As soon as the gateway is connected, the status on the configuration page will update accordingly:
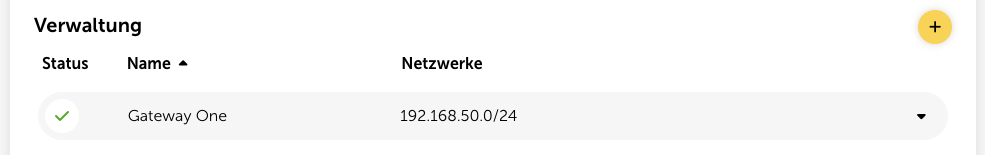
If you want to change a gateway's name or the networks to check, you can do this with the “Edit” button. Please note, though, that the IP addresses set in the first step can't be changed afterwards.
You can also delete gateways in this view. Click the yellow plus button to add more gateways that can be configured for other network ranges.